5. Sign on with LDAP¶
You can configure SystemLink to use the Lightweight Directory Access Protocol (LDAP) for user authentication. Use LDAP attributes and groups to map users to roles and workspaces in SystemLink's role based access control system.
5.1 Assumptions and Prerequisites¶
-
A server running SystemLink.
- Refer to Installing and Configuring SystemLink Server and Clients for the basics of setting up a SystemLink server.
-
Administrator desktop access to the SystemLink server.
-
An LDAP server accessible to the SystemLink server.
-
A bind user and bind password for the LDAP server.
- SystemLink supports anonymous connections. In this case the bind user and bind password are not needed.
-
Familiarity with the LDAP attributes available to your organization.
- If you do not know what LDAP attributes and groups are available to you, talk with your LDAP system administrator.
- Tools such ADExplorer can be helpful to explore the attributes assigned to your users.
5.2 Enabling LDAP in SystemLink¶
5.2.1 Configuring Authentication¶
-
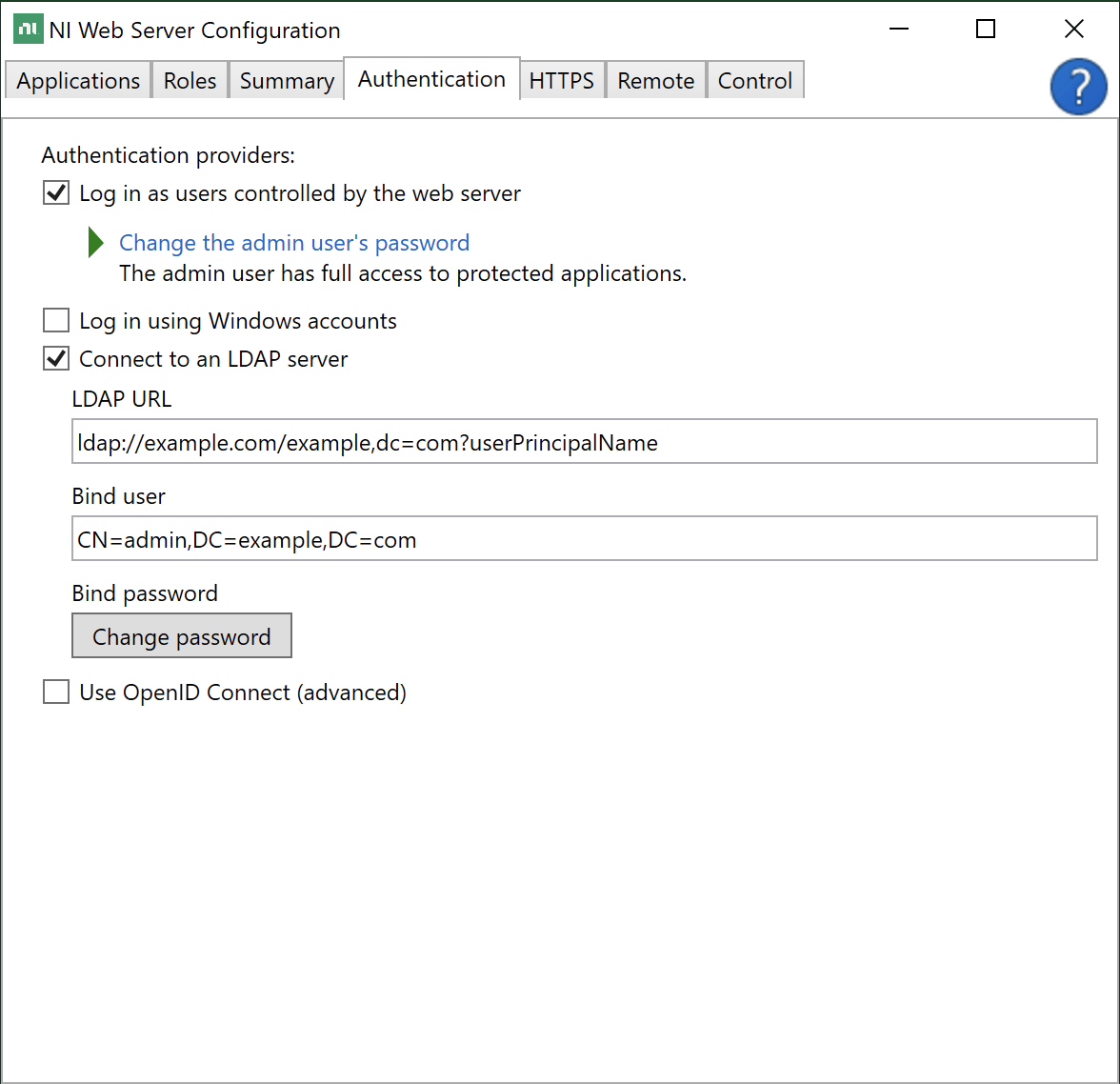
Log into the server running SystemLink and open NI Web Sever Configuration.
-
Go to the Authentication tab and enable Connect to an LDAP server.
-
Enter the LDAP URL for your sever. Refer to 5.3.1 LDAP URLs for details on how to structure this URL.
-
Enter the bind user. Refer to 5.3.2 Bind User for details on usernames that can be used here.
-
Enter the bind password.
-
Click Apply and Restart.
You may now log in to the SystemLink server using your LDAP credentials. To access systems and data in SystemLink, configure workspace and role mappings. Refer to Mapping LDAP Attributes and Groups to SystemLink Workspaces and Roles for details.
5.3 LDAP URL and Bind User¶
You must provide a URL and bind user and bind password to establish an authenticated connection between your SystemLink server and LDAP server.
5.3.1 LDAP URL¶
The LDAP URL follows a standard scheme.
URL Scheme
<ldap>://<server-dns>:<port>/<target-entry-dn>?<username-attribute>?<scope>?<filter>
protocol: ldap or ldaps for secure connections. SystemLink does not support STARTTLS, which allows connections over non-TLS and then initiates a TLS handshake.
server-dns: The LDAP server SystemLink is connecting to.
port: The port of the LDAP server. If your LDAP server is backed by Windows Active Directory, you may point to the global catalog on port 3268 to enable login from multiple domains (forest).
target-entry-dn: The base search distinguished name (DN) for the LDAP directory.
user-name-attribute: The attribute that determines the SystemLink username for login.
scope: The scope of the directory search. Scope defaults to sub but can be set to one to restrict users to the base DN.
filter: The LDAP search filter. This defaults to objectClass=* to find find all objects in the directory. This allows you to restrict login to users who have a specific attribute.
Basic LDAP URL Example
Example: ldap://example.com:389/dc=example,dc=com?sAMAccountName
In this example the server is example.com, the port is 389, the base search DN is dc=example,dc=com and the LDAP attribute used for user login is sAMAccountName.
Example LDAP URLs specifying different usernames for the user Jane Doe
URL: ldap://example.com/dc=example,dc=com?sAMAccountName
Username: jdoe
URL: ldap://example.com/dc=example,dc=com?userPrincipalName
Username: jane.doe@example.com
jdoe is used because the sAMAccountName attribute is specified in the LDAP URL.
If a username attribute is not specified NI Web Server Configuration will automatically add uid as the attribute. Depending on your LDAP directory setup this attribute may not be available.
5.3.2 Bind User¶
The bind user and bind password are used to authenticate with the LDAP server. Provide a distinguishedName or a userPrincipalName to specify the bind user. If the password for this user changes, NI Web Server Configuration must be updated for users to continue to log into SystemLink.
Bind user formats for the user Jane Doe
distinguishedName: cn=jdoe,dc=example,dc=com
userPrincipalName: jane.doe@example.com
5.4 Mapping LDAP Groups, Users, and Attributes to Workspaces and Roles¶
To add a user or collection of users to a workspace and assign a role you must complete the role mapping workflow.
-
Log in to the SystemLink web application with a user mapped to the Server Administrator role.
-
Go to Access Control > Workspaces and click the gear icon in the top right.
-
Create a new workspace or edit an existing workspace.
-
Go to the Role Mappings tab.
-
Click +MAPPING and select one of the available LDAP mapping types: LDAP Group, LDAP User, or LDAP Attribute.
-
If you have have selected LDAP Attribute enter a valid key and value. For LDAP User or LDAP Group enter a valid value.
5.4.1 LDAP Group Mapping¶
LDAP Group mapping queries the objectClass of group (Active Directory specific), groupOfName, and groupOfUniqueNames to match either member or uniqueMember attributes of the group.
!!! note Group names should be declared using the full LDAP distinguishedName of the group.
cn=Users,dc=example,dc=com
5.4.2 LDAP User Mapping¶
You may specify a LDAP username when creating workspace and role mappings. The username you specify is the same as the usernames for logging into SystemLink.
5.4.3 LDAP Attribute Mapping¶
You can use any available LDAP attribute to create a workspace and role mapping. In this case both the name and value of the attribute must match exactly for the mapping to be successful.
Example LDAP attribute mapping
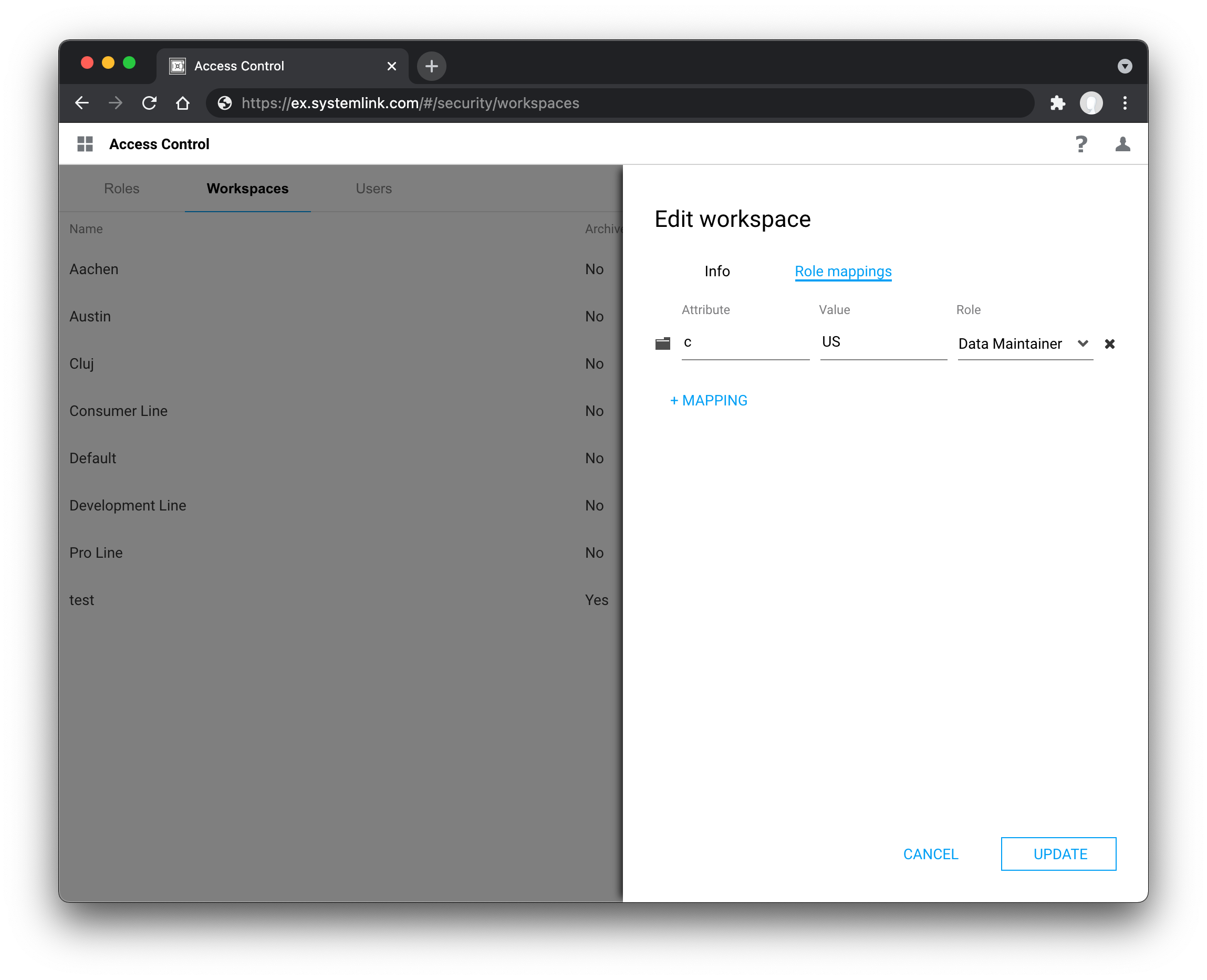
c with the value US to the Data Maintainer Role in the Default workspace.